- Download SniperSpy Keylogger - Best Remote Spy Software For Windows
- Download - SniperSpy Keylogger For Mac Users
- Download Spyphone Gold - Spy Cell Phones
- Hack a Remote Computers Using - Realtime Spy
- Hack a Remote Computers Using -Ardamax Keylogger
- Download Simple Binder - Binders Software to Bypass Antivirus Detection
- Download Stealth Crypter - Crypter Software To Bypass Antivirus Detection
SniperSpy Keylogger - Best Remote Spy Software
 Are you looking for the Best Remote password hacking software? Do you need to spy on your remote computer without the need for physical access? But wait! Before you go for any remote spy software you should read our shocking reviews!
Are you looking for the Best Remote password hacking software? Do you need to spy on your remote computer without the need for physical access? But wait! Before you go for any remote spy software you should read our shocking reviews!MCT Recommends the Following Software
SniperSpy Keylogger - Best Remote Spy Software
Sniper Spy (Remote Installation Supported )
SniperSpy is the industry leading Remote password hacking software combined with the Remote Install and Remote Viewing feature.Once installed on the remote PC(s) you wish, you only need to login to your own personal SniperSpy account to view activity logs of the remote PC’s! This means that you can view logs of the remote PC’s from anywhere in the world as long as you have internet access!
Do you want to Spy on a Remote PC? Expose the truth behind the lies! Unlike the rest, SniperSpy allows you to remotely spy any PC like a television! Watch what happens on the screen LIVE! The only remote PC spy software with a SECURE control panel!
This Remote PC Spy software also saves screenshots along with text logs of chats, websites, keystrokes in any language and more. Remotely view everything your child, employee or anyone does while they use your distant PC. Includes LIVE admin and control commands!
SniperSpy Features
1. SniperSpy is remotely-deployable spy software
3. Logs All Keystrokes
4. Records any Password (Email, Login, Instant Messenger etc.)
5. Remote Monitor Entire IM Conversations so that you can spy on IM activities too
6. Captures a full-size jpg picture of the active window however often you wish
7. Real Time Screen Viewer
8. Remotely reboot or shutdown the PC or choose to logoff the current Windows user
9. Completely Bypasses any Firewall
What If i don't have physical access to victims computer?
No physical access to your remote PC is needed to install the spy software. Once installed you can view the screen LIVE and browse the file system from anywhere anytime. You can also view chats, websites, keystrokes in any language and more, with screenshots.
This software remotely installs to your computer through email. Unlike the other remote spy titles on the market, SniperSpy is fully and completely compatible with any firewall including Windows XP, Windows Vista and add-on firewalls.
The program then records user activities and sends the data to your online account. You login to your account SECURELY to view logs using your own password-protected login. You can access the LIVE control panel within your secure online account.
Why Do I need This Software?
- For Partners: Do you Suspect that your Spouse is cheating on you AND you do not have hard evidence to prove it? Consider Installing SniperSpy, it not only gives you the Complete activity of your Spouse but also provides enough Screen shots and Chat history that can serve as the clear evidence against your Cheating Spouse
- For Parents: Does your child spends most of their time before their computers? If your children spend time chatting or playing computer games, they can be approached by the strangers. In other words they are exposed to potentially Dangerous things like PORN, Gambling, Dating Strangers, etc. In this Case SniperSpy is the best solution to Monitor and control the Online Activity of your child.
- For Employers: Do all your employees use their computer resources and Internet connection solely for your business? Do they work as hard as you? OR Do you suspect your employee’s productivity is lacking? You should consider installing This Remote Software that can serve as the best Employee Monitoring Software for Small business.
- For Hackers: Are you looking for any easy way to hack into someones facebook or Myspace accounts ? or wanna control someones facebook account? SniperSpy can expose you all the Keystrokes entered by your victim including Usernames and Passwords for any websites.
So what are you waiting for! Grab a copy of Snipersspy and start Monitoring your friends .For download details kindly visit the following link
If You have any doubts Regarding the installation, Please feel free to post a comment
Download - SniperSpy Keylogger For Mac Users
I have previously written a review on SniperSpy Keylogger and concluded that it is the best key-logger to hack Face book,Gmail or any other email account password. Unfortunately many of blog readers were using Mac OS and Sniperspy was not compatible with Mac os,
But now after continuous pressure from costumers all around the world Sniperspy has finally released a version of Sniperspy keylogger for Mac users
Download Sniper-Spy For MAC Users
But now after continuous pressure from costumers all around the world Sniperspy has finally released a version of Sniperspy keylogger for Mac users
Are you worried how others might use your Mac OS X computer? Expose the truth behind the lies! SniperSpy is the only software that allows you to secretly watch your Macintosh like a television! Login from ANYWHERE using another computer, smart phone or iPad.
View the screen LIVE and see everything they do online in real time! Browse the file system, view chats, websites, keystrokes and more, with screen shots You can also access the LIVE control panel within your secure online account to perform live monitoring functions.
SniperSpy Mac runs in COMPLETE STEALTH MODE making the program completely hidden. There are no mentions of the program anywhere on your Mac. The following are some of the other features of SniperSpy
Live Screen Viewer
By far the most effective feature of the application, the LIVE screen viewer allows you to see the entire screen of your Mac in real time.
Keystrokes Typed
The Keystroke log will display all of the keystrokes recorded in any open window, application, or Internet browser
Chat Transcripts
SniperSpy records all chat conversations of Gmail , Skye,Yahoo, MSN etc
SniperSpy Mac has many more features. I have only mentioned a few
Download !!
So if your a Mac user, grab a copy of SniperSpy Mac Keylogger and start hacking your friends, For more information and download details kindly visit the following link
Note :- This version of keylogger works only with Mac os If your looking for a Windows keylogger i suggest you to have a look at SniperSpy Keylogger for windows , Realtime spy Keylogger
SniperSpy records all chat conversations of Gmail , Skye,Yahoo, MSN etc
SniperSpy Mac has many more features. I have only mentioned a few
Download !!
So if your a Mac user, grab a copy of SniperSpy Mac Keylogger and start hacking your friends, For more information and download details kindly visit the following link
Note :- This version of keylogger works only with Mac os If your looking for a Windows keylogger i suggest you to have a look at SniperSpy Keylogger for windows , Realtime spy Keylogger
Spy Cell Phones with Spyphone Gold
 Spyphone Gold (Spyera gold) is the most advance cell phone keylogger on the market today. This is based on its supercharged features,reputation and great system core stability.It has been in the business of developing phone spy applications for over ten years which makes it one of oldest companies in this particular market. During this time Spyera’s engineering team has ensured that this product remained one of the leaders in the development of new phone spy features and also phone compatibility (e.g. Spyera was the first Blackberry spy app to work on O/S 6). Basically if you would like to monitor virtually any cell phone in any location in the world then Spyera is the way to go.
Spyphone Gold (Spyera gold) is the most advance cell phone keylogger on the market today. This is based on its supercharged features,reputation and great system core stability.It has been in the business of developing phone spy applications for over ten years which makes it one of oldest companies in this particular market. During this time Spyera’s engineering team has ensured that this product remained one of the leaders in the development of new phone spy features and also phone compatibility (e.g. Spyera was the first Blackberry spy app to work on O/S 6). Basically if you would like to monitor virtually any cell phone in any location in the world then Spyera is the way to go.
Who Uses This product?
Virtually anyone who has suspicions that their partner is cheating, employee is stealing or children are being led astray can use Spyera. There are other phone surveillance apps on the market but what makes this one different is the fact that you will be able to intercept live phone calls. This means that you will hear every single nitty gritty detail in the call without the participants knowing. If you combine this function with the other features of this product, you will know beyond a shadow of a doubt if that person is guilty of any wrong doings. Intercepting other communications are great but it is nothing better than listening in to a cell phone conversation. After you discover what you were looking for you will be able to take appropriate action.
How Does Spyphone Gold Work?
How Does Spyphone Gold Work?
If you need to listen into a phone conversation you will just have to dial into the target phone during the call and you will be added to the conversation. Don't worry you will be notified via sms message that the call is in place.
Features
- Spy phone calling - This is the ability to call the phone and listen to the surroundings of the phone. Therefore if the person is in traffic you will hear horns blowing etc and you will confirm what they are up to.
- Call Interception (Listen to Phone Call) – this Spyera feature enables you to secretly liste to incoming & outgoing calls.
- Remote Monitoring – want to find out what is going on “around” the iPhone? This remote listening feature is how you do it.
- SMS Logging (Incoming / Outgoing) – this will enable you to read all text messages, even if they are deleted.
- Call History (Incoming / Outgoing) – get access to all incoming and outgoing call logs to find out their calling habits.
- Call Duration (Incoming / Outgoing) – this will give you visibility into how much time they are spending on each call.
- GPS and Cell ID Location Tracking – this Spyera feature will secretly track the iPhone in real time.
- Email Logging (Incoming / Outgoing) – want to know who they are emailing & what they are sending? This feature will show you.
- Contact Name in Address Book Linked to each call/sms – View the contact details of everyone they contact.
- SIM Change SMS Notification – If your target ever changes their SIM card, Spyera Gold will notify you & send you their new number.
- %100 Undetectable – No chance they will find out Spyera is on their iPhone. Spyera Gold is 100% undetectable!
- Remote Control – Control Spyera (activate spy call, uninstall, etc..) via remote SMS commands.
- 10 Days %100 Money Back Guarantee – Spyera stands behind their iPhone spy product.
- Unlimited device change – This will ensure that if your target changes their phone, you’ll be able to monitor their new one.
Compatible Cell Phones
Spyphone Gold is fully compatible with the following mobile phones
- Nokia, LG, Samsung and Sony Ericsson Phones
- BlackBerry Phones
- Apple iPhones
- Windows Mobile Phones
Download Spyphone-Gold
So what are you waiting for! Grab a copy of Spyphone gold and start spying your friends ,spouse cellphones
Hack a Remote Computer Using Realtime Spy
In one of my previous tutorials we discussed how we can use ardamax key logger to hack remote computers .In this article i will explain What is Realtime spy and i will also explain How you can use Real time spy to hack remote computers
What is Real time Spy ?
Hack a Remote Computer Using Realtime Spy :-
How To Hack a Remote Computer Using Ardamax Keylogger
In my previous post i gave my blog readers free Ardamax keylogger software.which can be used to hack remote computer,Basically Keylogger is a software that is installed on a Victims computer without his knowing, this Keylogger software simply keeps on recording the Key strokes typed by the victim and sends them to your mailbox. No doubt, these keystrokes contain the victim’s Email passwords and All such important information.Hence you can hack your friends Email account passwords and various other passwords. To know more about Keyloggers you can read my article What are Keyloggers
In this article i will explain how you can Install Ardamax keylogger remotely on victims PC
Hack a Remote Computer Using Ardamax Keylogger
What is Real time Spy ?
Realtime-Spy is the latest in cutting-edge remote spy software monitoring technology that allows you to monitor ANY PC you own from ANYWHERE. Realtime-Spy is remotely installable .It is one of the best and the Cheapest spying softwares which is out there in the market
Why Realtime spy ?
So now you will ask me, why i should use Realtime spy ? If i can do the same using Ardamax keylogger for a free of cost .The answer is going to be very simple ,In Ardamax keylogger there are only few features that you can use to monitor remote computers , It can be easily found by using Antivirus programs and moreover it needs physical access for instillation
But in Realtime spy no physical installation is needed .It also has some excellent features like its activity logs are accessible from anywhere regardless if the remote PC is online or not , Realtime-Spy logs all keystrokes, websites visited, applications ran, e-mail activity, chat conversations, screenshots, and many more
Its stealth (i.e) it's totally undetectable by anti viruses.The best feature i like in Realtime-Spy is it can show you what users are doing, and typing, in real-time. So overall ardamax keylooger is no comprision to Realtime-Spy
Hack a Remote Computer Using Realtime Spy :-
Step 1 :-
First a fall Download Realtime-Spy from Here. After downloading your copy of Realtime-Spy navigate to where you downloaded (in this case it is on the Windows desktop). Double click the Realtime-Spy installer file to start the install.
NOTE: After install is complete you can delete this file!
Step 2:-
Upon finishing the installation you will be able to run Realtime-Spy's configuration file immediately. Do this and continue to the next step.
Step 3 :-
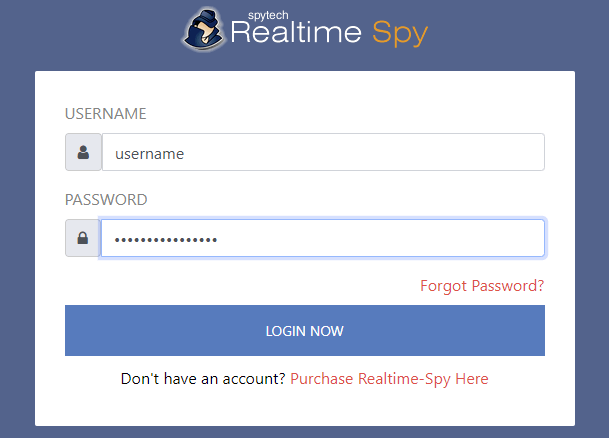
You will now see the Realtime-Spy configuration window. Enter in your username and password that you received after purchasing Realtime-Spy. These must be entered EXACTLY as given. They are case sensitive, and take care not to mix up 0's with O's and I's with l's.
After you enter your username and password, choose whether or not you want Realtime-Spy to display a splash warning whenever it is ran, and how often you want it to clear its logs.
After you enter your username/password and select the options you want - press "next" to go to the next configuration panel.
Step 4 :-
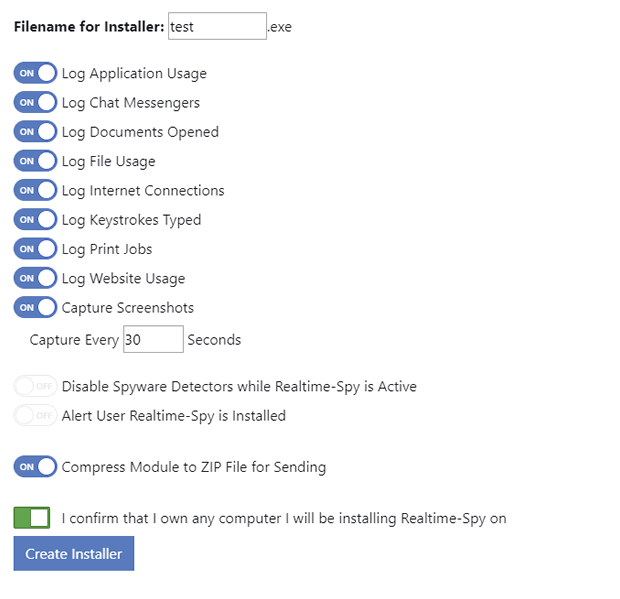
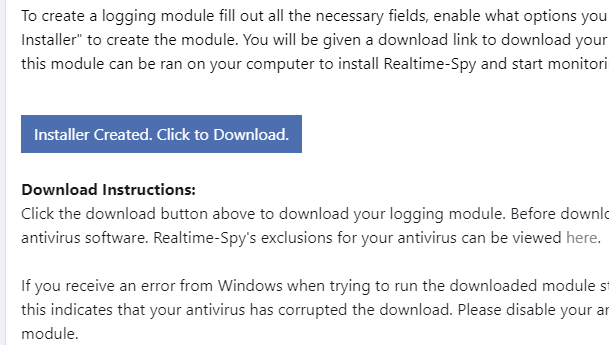
When you click "next" Realtime-Spy will verify your settings. If they are correct you will be able to configure your monitoring options, as shown below. Once you have your options set click "create" to create your logging module.
Step 5 :-
Click "create" to create your logging module. You will be prompted for a name to give the file you are creating. In this example we have named it 'test' - you can name it whatever you want. Click Save and you will receive a message similar to the one below.
Remember the location of the file you have just created!
Step 6 :-
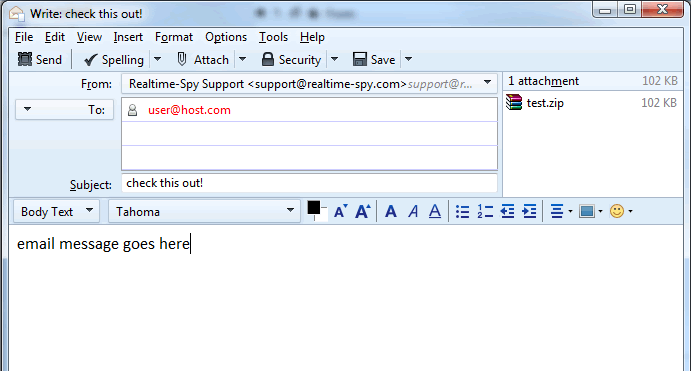
Now it is time to send out the file to the remote PC. In this guide we are using Outlook Express on Windows XP.
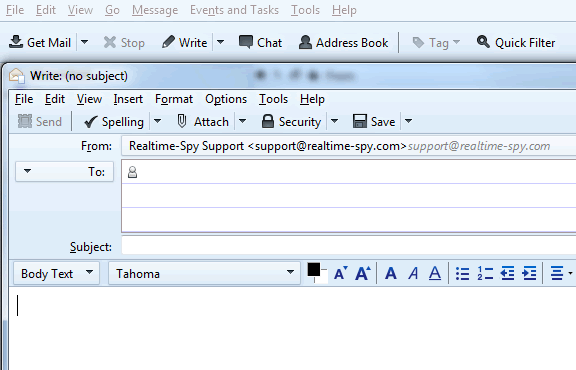
Click the Create Mail button to open a new mail window.
Step 7 :-
Click ATTACH and navigate to where you saved your Realtime-Spy file you created previously. Click on the file and then click 'Attach' to attach the file to your email.
Step 8 :-
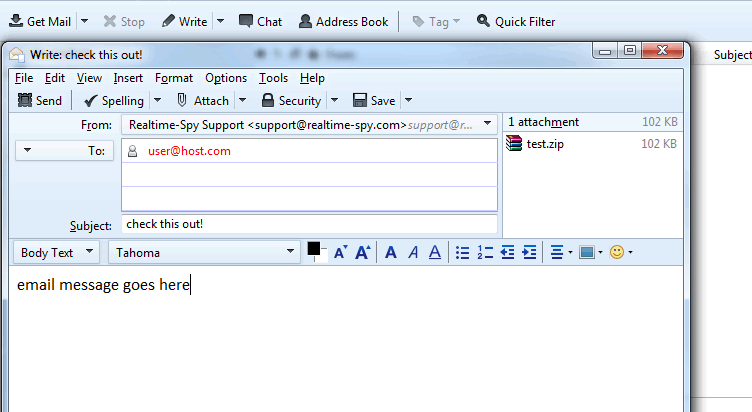
You will now have to enter a recipient for the file you are sending, as well as an email subject and body. Notice the size of the Realtime-Spy file - it should be approximately 100-120kb at all times!
Once you are ready to go click Send to send the email!
Step 9 :-
Once you send out the file you can then login to your Realtime-Spy webspace. This is located at www.realtime-spy.com/mems/
Enter in your username/password at the prompt to continue!
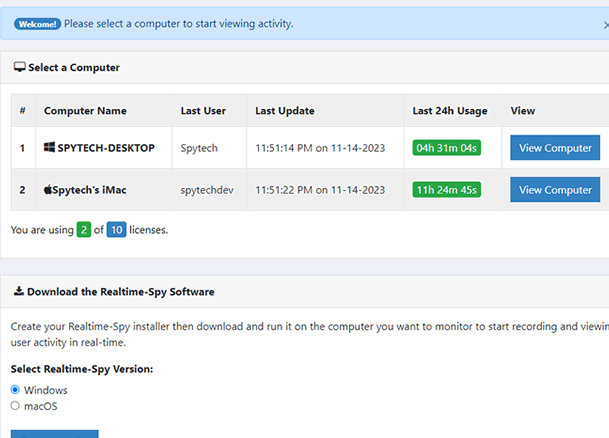
Step 10 :-
You will be presented with your Realtime-Spy webspace. Here you can select and view users that were logged with the file you sent out.
Note: Users will only appear after they have downloaded and executed the file you have sent them.
First a fall Download Realtime-Spy from Here. After downloading your copy of Realtime-Spy navigate to where you downloaded (in this case it is on the Windows desktop). Double click the Realtime-Spy installer file to start the install.
NOTE: After install is complete you can delete this file!
Step 2:-
Upon finishing the installation you will be able to run Realtime-Spy's configuration file immediately. Do this and continue to the next step.
Step 3 :-
You will now see the Realtime-Spy configuration window. Enter in your username and password that you received after purchasing Realtime-Spy. These must be entered EXACTLY as given. They are case sensitive, and take care not to mix up 0's with O's and I's with l's.
After you enter your username and password, choose whether or not you want Realtime-Spy to display a splash warning whenever it is ran, and how often you want it to clear its logs.
After you enter your username/password and select the options you want - press "next" to go to the next configuration panel.
Step 4 :-
When you click "next" Realtime-Spy will verify your settings. If they are correct you will be able to configure your monitoring options, as shown below. Once you have your options set click "create" to create your logging module.
Step 5 :-
Click "create" to create your logging module. You will be prompted for a name to give the file you are creating. In this example we have named it 'test' - you can name it whatever you want. Click Save and you will receive a message similar to the one below.
Remember the location of the file you have just created!
Step 6 :-
Now it is time to send out the file to the remote PC. In this guide we are using Outlook Express on Windows XP.
Click the Create Mail button to open a new mail window.
Step 7 :-
Click ATTACH and navigate to where you saved your Realtime-Spy file you created previously. Click on the file and then click 'Attach' to attach the file to your email.
Step 8 :-
You will now have to enter a recipient for the file you are sending, as well as an email subject and body. Notice the size of the Realtime-Spy file - it should be approximately 100-120kb at all times!
Once you are ready to go click Send to send the email!
Step 9 :-
Once you send out the file you can then login to your Realtime-Spy webspace. This is located at www.realtime-spy.com/mems/
Enter in your username/password at the prompt to continue!
Step 10 :-
You will be presented with your Realtime-Spy webspace. Here you can select and view users that were logged with the file you sent out.
Note: Users will only appear after they have downloaded and executed the file you have sent them.
If you have any doubts regarding the Installation . Please feel free to post a comment
How To Hack a Remote Computer Using Ardamax Keylogger
In my previous post i gave my blog readers free Ardamax keylogger software.which can be used to hack remote computer,Basically Keylogger is a software that is installed on a Victims computer without his knowing, this Keylogger software simply keeps on recording the Key strokes typed by the victim and sends them to your mailbox. No doubt, these keystrokes contain the victim’s Email passwords and All such important information.Hence you can hack your friends Email account passwords and various other passwords. To know more about Keyloggers you can read my article What are Keyloggers
In this article i will explain how you can Install Ardamax keylogger remotely on victims PC
Hack a Remote Computer Using Ardamax Keylogger
Things we Need : -
1. Ardamax keylogger Download from Here
(Update :- You can also download the latest version of Ardamax Keylogger (FUD) from Here)
2. Ftp account - You can create a free ftp account from www.drivehq.com
3. Crypter Software - To disable antivirus detection .You can Downland Crypter Software from Here
Procedure :-
1. After installing Ardamax keylogger, select and right click Ardamax keylogger icon from your tasks bar. Now select enter registration key , then put in the name and the serial number which you will get from the downloaded software folder
2. Now right click Ardamax keylogger icon and select remote installation, click next two times check all the boxes as shown then finally click next
4. Now enter your ftp account details which you created earlier in my case in enter Ftp host -ftp.drivehq.com ,remote folder -/logs ,user - test, Finally click next
1. Ardamax keylogger Download from Here
(Update :- You can also download the latest version of Ardamax Keylogger (FUD) from Here)
2. Ftp account - You can create a free ftp account from www.drivehq.com
3. Crypter Software - To disable antivirus detection .You can Downland Crypter Software from Here
Procedure :-
1. After installing Ardamax keylogger, select and right click Ardamax keylogger icon from your tasks bar. Now select enter registration key , then put in the name and the serial number which you will get from the downloaded software folder
2. Now right click Ardamax keylogger icon and select remote installation, click next two times check all the boxes as shown then finally click next
3. Now click enable and enter a password so that no one can open the keylogger then click next three times, check "send logs every " and set your time say 5 min , Then select delivery method as Ftp, finally click next
4. Now enter your ftp account details which you created earlier in my case in enter Ftp host -ftp.drivehq.com ,remote folder -/logs ,user - test, Finally click next
5. Now check all the boxes and click next, set your time for capturing the screen shots, then click next, If you want you can also change the icon by selecting change icon as shown. Finally select next and click finish
6. If you've done all the steps correctly, you should get a server file (keylogger file ) , But this server file can be easily detected by anti -viruses , So to bypass anti viruses we need to bind and crypt the file ,So to do this open your crypter software (which you downloaded earlier) Now select file 1 as the server file (key logger file which you created) and then select file 2 as any application, select a good application(select a PDF file for best performance)finally click Crypt file, Now you will get a crypted server file ( key logger file ) which is FUD ( I.e ) Fully undetectable by anti viruses
7. Now send the fully undetectable Server file(keylogger file ) to your victim via email or upload it to any site and ask the victim to download the file.Once the victim clicks the application .Ardamax keylogger will automatically install and will send logs(containing facebook password email passwords ,chat logs ..etc) to
your ftp account .You can view your victims logs by going to your ftp account
6. If you've done all the steps correctly, you should get a server file (keylogger file ) , But this server file can be easily detected by anti -viruses , So to bypass anti viruses we need to bind and crypt the file ,So to do this open your crypter software (which you downloaded earlier) Now select file 1 as the server file (key logger file which you created) and then select file 2 as any application, select a good application(select a PDF file for best performance)finally click Crypt file, Now you will get a crypted server file ( key logger file ) which is FUD ( I.e ) Fully undetectable by anti viruses
7. Now send the fully undetectable Server file(keylogger file ) to your victim via email or upload it to any site and ask the victim to download the file.Once the victim clicks the application .Ardamax keylogger will automatically install and will send logs(containing facebook password email passwords ,chat logs ..etc) to
your ftp account .You can view your victims logs by going to your ftp account
Note:- After crypting if this Keylogger is still detected by your anti-viruses, Then please use Rinlogger (Free Keylogger ) which is 100% FUD from HereThis is a simple but a very effective method of hacking a remote computer.If you have any doubts please be free to post a comment
Binder software to disable Antivirus detection
Whats A Binder ?
Binder is a software used to bind or combine two or more files in one file under one name and extension. The files to be binded can have any extension or icon. The user has choice to select the name, icon and various attributes of binded file. If binded file contains an application (in our case - RAT or keylogger), the application is also run when the actual binded file is run.thus Binder is used to bypass antivirus detection.
How To Use Simple Binder
1. First of all, you need a binder. So, download free Binder software.
2. To get the password Click here
3. Install software on your computer to see:
4. Now, click on "Select File #1" and select the keylogger or RAT you wanna bind to avoid its antivirus detection.
5. Click on "Select File #2" and select the normal file with which you wanna bind our Trojan, RAT or Keylogger.
6. Simply, hit on "Bind" to obtain the binded keylogger or Trojan file. Now, simply send this file to victim whom this file will appear normal (Trojan is hidden due to binding).
7. Remember to check both "Execute"options and you can use "EXE Pump" to increase your file size to desired value.
Note:-
If you have any doubts regarding this article , Please pass your comments for clarifications
2. To get the password Click here
3. Install software on your computer to see:
5. Click on "Select File #2" and select the normal file with which you wanna bind our Trojan, RAT or Keylogger.
6. Simply, hit on "Bind" to obtain the binded keylogger or Trojan file. Now, simply send this file to victim whom this file will appear normal (Trojan is hidden due to binding).
7. Remember to check both "Execute"options and you can use "EXE Pump" to increase your file size to desired value.
Note:-
- You can use this software to bind Ardamax keylogger
- You can also use crypter to bypass antivirus detection
If you have any doubts regarding this article , Please pass your comments for clarifications
Crypter Software To Bypass Antivirus Detection
What is Crypter?
Crypter is a software used to hide our viruses, keyloggers or tools from antiviruses so that they are not detected by antiviruses. Thus, a crypter is a program that allow users to crypt the source code of their program. Generally, antivirus work by splitting source code of application and then search for certain string within source code. If antivirus detects any certain malicious strings, it either stops scan or deletes the file as virus from system.
What does Crypter do?
Crypter simply assigns hidden values to each individual code within source code. Thus, the source code becomes hidden. Hence, our crypted file becomes UD (undetactable ) or FUD (fully undetectable )
UD means undetected, so only a few antivirus programs detect it. FUD means fully undetected, so no antivirus detects it
UD -Stealth Crypter - Download
1. First download Stealth Crypter from Here
2. To get the password click here
3. Install software on your computer
4. Now, click on "Select File #1" and select the keylogger or RAT you wanna crypt to avoid its antivirus detection.
5. Click on "Select File #2" and select the normal file with which you wanna bind our trojan, RAT or Keylogger.
6. If you want you can also change the icon ( i have included the icon pack also ) Finally, hit on "crypt" to . make the file UD
Note :-
If you have any doubts ,please feel free to post a comment
Crypter is a software used to hide our viruses, keyloggers or tools from antiviruses so that they are not detected by antiviruses. Thus, a crypter is a program that allow users to crypt the source code of their program. Generally, antivirus work by splitting source code of application and then search for certain string within source code. If antivirus detects any certain malicious strings, it either stops scan or deletes the file as virus from system.
What does Crypter do?
Crypter simply assigns hidden values to each individual code within source code. Thus, the source code becomes hidden. Hence, our crypted file becomes UD (undetactable ) or FUD (fully undetectable )
UD means undetected, so only a few antivirus programs detect it. FUD means fully undetected, so no antivirus detects it
UD -Stealth Crypter - Download
1. First download Stealth Crypter from Here
2. To get the password click here
3. Install software on your computer
4. Now, click on "Select File #1" and select the keylogger or RAT you wanna crypt to avoid its antivirus detection.
5. Click on "Select File #2" and select the normal file with which you wanna bind our trojan, RAT or Keylogger.
6. If you want you can also change the icon ( i have included the icon pack also ) Finally, hit on "crypt" to . make the file UD
Note :-
- You can use this software to bind Ardamax keylogger
- You can also use a Binder software to Bypass Antivirus detection
- This is only a UD crypter so some anti-viruses will detect your key loggers/viruses even after crypting
If you have any doubts ,please feel free to post a comment



















in stealth crypter it doesnt bypass the antivirus detection
ReplyDeleteIf you need a parental control tool, you can search the Internet and find many. Some websites browsers or social networks have parental control functions. If you want to realize parental control on PC,I recommend you to try professional third party software which has functions of site block and time control,etc.I have used parental control program of anykeylogger(www.anykeylogger.com),it works well,you can also find other fine programs on the Internet.
ReplyDeleteI truly delighted in perusing this post, enormous fan. Keep doing awesome me when would you be able to distribute more articles or where would I be able to peruse more on the subject? cellulari spia
ReplyDelete